Thought Leadership
Search below for technical content and industry interviews
Find Content
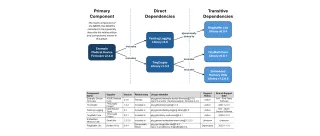
Software Transparency and SBOMs
Software transparency is critical to securing modern medical devices. SBOMs provide visibility into the software components that make up a device, enabling better supply chain oversight, faster vulner... ...more
Cybersecurity ,Blogs &Security Guides
December 15, 2025•3 min read

Cybersecurity Labeling for Medical Devices
Cybersecurity labeling connects design intent to real-world device use. It communicates to clinicians, IT administrators, and healthcare delivery organizations how to install, configure, maintain, and... ...more
Cybersecurity ,Blogs &Security Guides
October 14, 2025•9 min read

Design-Time Security Risk Management for Medical Devices
By identifying and mitigating risks at design time, manufacturers avoid embedding vulnerabilities into their systems and ensure compliance with international regulations and standards. ...more
Cybersecurity ,Blogs &Security Guides
September 24, 2025•13 min read

VEL-CAL: Cryptographic Assurance Levels
The Velentium Medical Cryptographic Assurance Levels (VEL-CAL) framework defines a tiered classification system for selecting cryptographic primitives and configurations in medical device systems. ...more
Cybersecurity ,Blogs &Security Guides
August 23, 2025•6 min read
Total Product Life-Cycle Security for Medical Devices
Cybersecurity isn’t just a test before launch. At Velentium Medical, it’s built into every phase of development and maintenance. Our Total Product Life-Cycle process ensures your device is secure by d... ...more
Cybersecurity ,Blogs &Security Guides
August 04, 2025•2 min read

Mastering the Art of Budgeting for Your Medtech Startup
Starting a medtech company? You're about to venture into a world that blends healthcare advances with business savvy. In a recent Velentium Medical Webinar, hosted by Dan Purvis, startup founders were... ...more
Webinars ,Blogs
July 25, 2025•2 min read
Safe. Secure. Effective.
One stop for secure Medical Device R&D, product development, contract
manufacturing, and postmarket services
Who We Are
© 2026 Velentium, LLC. All Rights Reserved.
