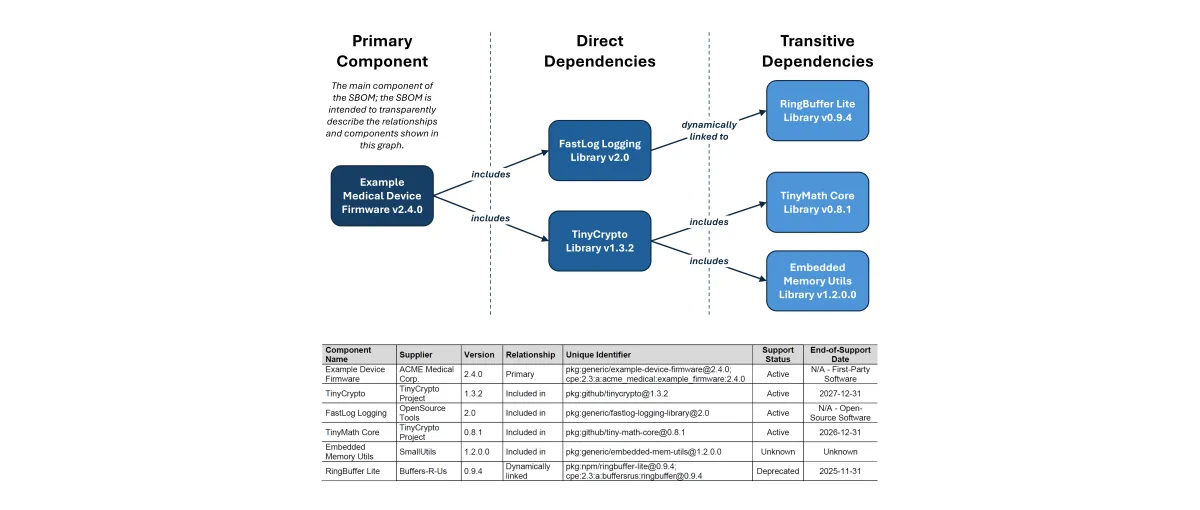
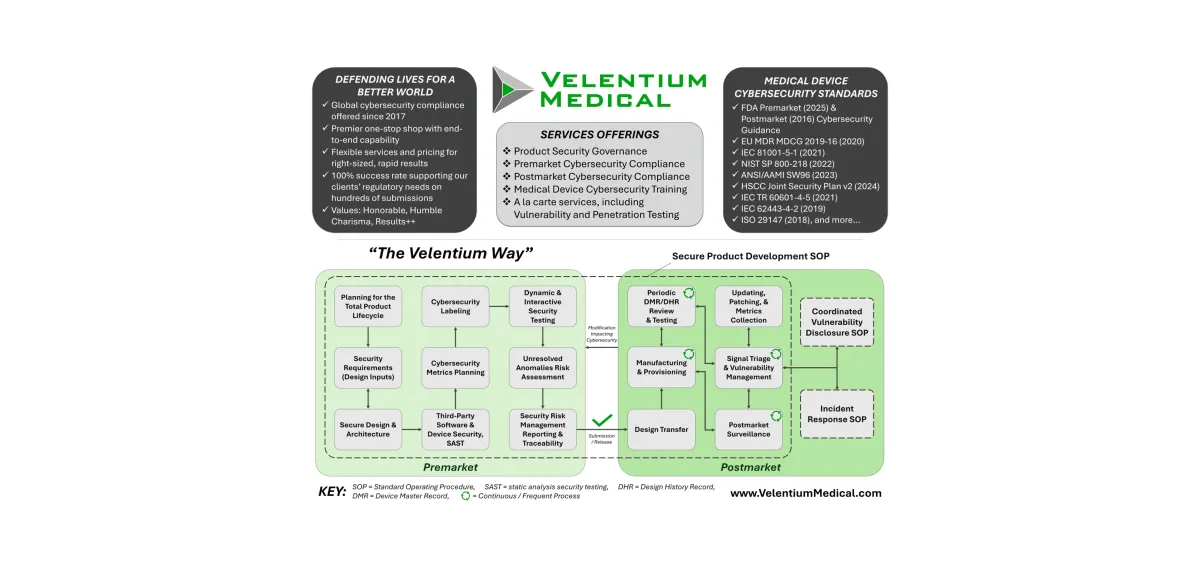
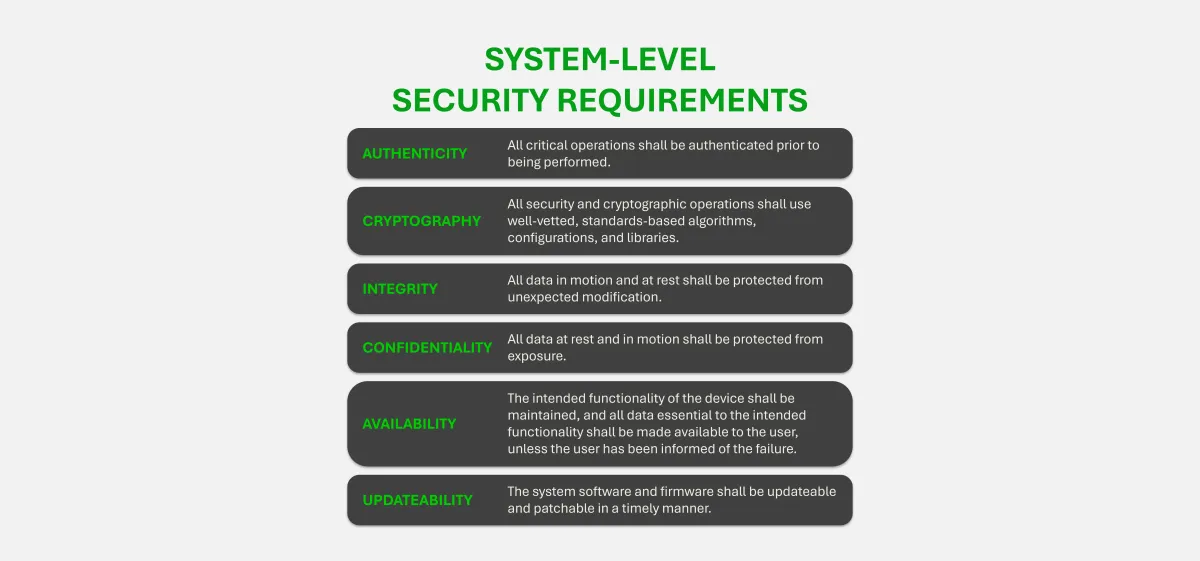
Software Transparency and SBOMs
Software transparency is critical to securing modern medical devices. SBOMs provide visibility into the software components that make up a device, enabling better supply chain oversight, faster vulnerability response, and greater trust between manufacturers and healthcare organizations. This content explores how SBOMs support these goals in practice.